WordPress is the world’s most popular content management system. It’s also one of the most popular targets for hackers and other malicious actors. In this tutorial, you’ll learn about five ways to make your WordPress site more secure.
Disclaimer: This review contains affiliate links, and I will receive a commission if you proceed with a purchase after clicking on an affiliate link. Thank you in advance for your support!
Change Your WordPress Login URL
By default, the login page for your WordPress site can be found at domain.com/wp-login.php. As a result of WordPress’ popularity, the default login page is a huge attack surface, and is often the target for malicious bots. Having your WordPress login page brute-forced by bots has obvious security implications, but there are also performance concerns as well. Since the wp-login.php page is bypassed from the page cache at most hosting providers, continuous hits on wp-login.php can result in CPU and RAM spikes.
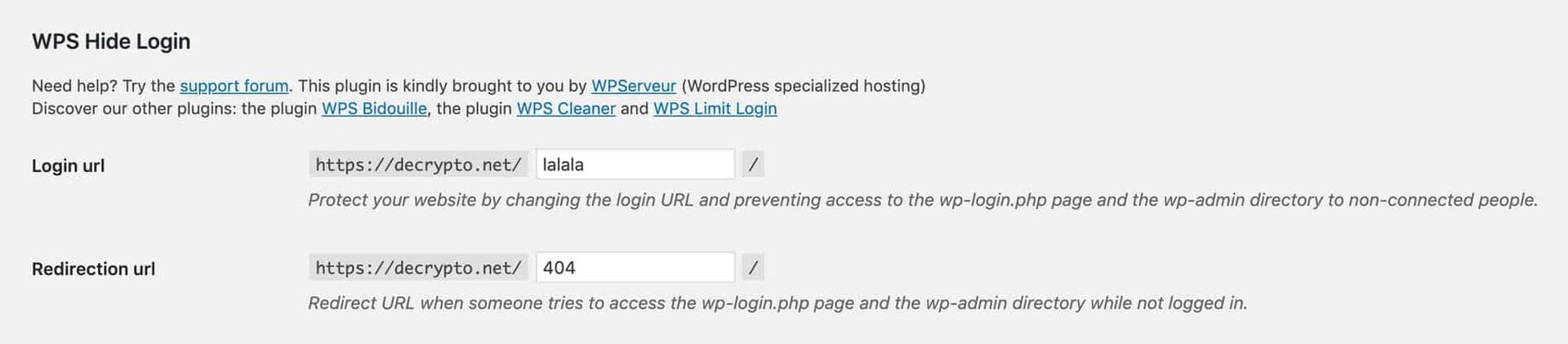
Change your WordPress login URL with WPS Hide Login.[/caption] The best way to change your WordPress login URL is to use the WPS Hide Login plugin. After installing the plugin, you can change the login URL to anything you want. WPS Hide Login also lets you specify a redirection URL which will automatically redirect anyone who tries to access wp-login.php.
Don’t Install Nulled Plugins & Themes
You should only install plugins and themes from trusted sources like the WordPress repository, a developer’s personal store, or a reputable marketplace like ThemeForest. You should never install plugins sourced from sketchy forums, Reddit groups, or that friend who’s an expert at pirating software. This is especially true for premium paid plugins. Just think about it. Someone had to pay for that plugin at one point or another, so it doesn’t make sense that it would be free for you. Nulled plugins and themes are often injected with malware that can be used to take control of your website. That’s why they’re “free”.
Block Access to xmlrpc.php
XML-RPC is a feature that lets WordPress interact with other apps and services. For example, the WordPress iOS app uses XML-RPC to establish a connection to your WordPress site, so you can can edit posts and upload images on the go. To support XML-RPC, WordPress core comes with an xmlrpc.php file. Like the wp-login.php file mentioned earlier, xmlrpc.php is also a huge attack surface for two main reasons.
- Since
xmlrpc.phpcan be used to gain remote access to your WordPress site, malicious actors can brute-forcexmlrpc.phpwith different username and password combinations. xmlrpc.php’s pingback feature can also be used to trigger DDoS attacks.
When it comes to xmlrpc.php usage, it’s better to follow a “whitelist-only” protocol. This way, you can whitelist certain IP addresses and user agents for xmlrpc.php access. If you’re managing your own server, you can create access rules in the NGINX or Apache configuration file. If you used a managed WordPress host, xmlrpc.php should already be blocked by default. If you’re on a managed WordPress host that leavesxmlrpc.phpwide open, considering switching to a host that takes security more seriously - Kinsta, Flywheel, etc.
Use a Web Application Firewall
Cloudflare and Sucuri are two companies that offer a comprehensive set of security features including a web application firewall (WAF). A WAF is your website’s first line of defense, and I highly recommend adding one to your WordPress site. While I’ve never used Sucuri’s offering, I use Cloudflare on all my sites. For my sites, I use the free plan, but for more serious sites like this one, I opt for the $20/month pro plan. In addition to more security tools, Cloudflare’s pro plan also comes with image optimization features, 20 page rules, and more. It’s a great value, and it puts my mind at ease.

Adding Cloudflare to your WordPress site is easy. All you have to do is create an account on Cloudflare, add a site, and then switch your domain’s nameservers to Cloudflare’s nameservers. If you’re looking for a more detailed guide on how to use Cloudflare, check out Kinsta’s tutorial.
Keep Everything Updated
Last but not least, you should always remember to keep WordPress core, plugins, and themes updated. Software is an ever-evolving beast, and new vulnerabilities are discovered everyday. Just in the last few months, we’ve seen major exploits in Social Warfare and Yuzo Related Posts. New versions were released quickly, but it’s probable that many WordPress users are still running old versions of the plugins that may contain exploits. I recommend doing a scan of your WordPress site for updates once a week. The process literally takes less than five minutes, and has the potential to save you a lot of time and frustration. If you’re low on time and manage a lot of WordPress sites, ManageWP has a dashboard solution that lets you update core, plugins, and themes in bulk. Security doesn’t have to be difficult if you don’t purposely make it difficult. As a recap, changing your login URL, avoiding nulled plugins and themes, blocking access to xmlrpc.php, using a web application firewall, and keeping your site updated are five ways you can keep your WordPress site more secure.